|
This content has been machine translated dynamically. Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. Cet article a été traduit automatiquement de manière dynamique. Este artículo lo ha traducido una máquina de forma dinámica. 此内容已经过机器动态翻译。 このコンテンツは動的に機械翻訳されています。 이 콘텐츠는 동적으로 기계 번역되었습니다. Este texto foi traduzido automaticamente. Questo contenuto è stato tradotto dinamicamente con traduzione automatica. This article has been machine translated. Dieser Artikel wurde maschinell übersetzt. Ce article a été traduit automatiquement. Este artículo ha sido traducido automáticamente. この記事は機械翻訳されています. 이 기사는 기계 번역되었습니다. Este artigo foi traduzido automaticamente. 这篇文章已经过机器翻译. Questo articolo è stato tradotto automaticamente.
Translation failed!
SAML for single sign-on with Citrix Files January 30, 2025 Contributed by: C K K Disclaimer: This feature will be deprecated if ShareFile (now Progress) discontinues support. You can configure Citrix Endpoint Management and ShareFile to use the Security Assertion Markup Language (SAML) to provide single sign-on (SSO) access to Citrix Files mobile apps. This functionality includes: Citrix Files apps that are MAM SDK enabled or wrapped by using the MDX Toolkit
Non-wrapped Citrix Files clients, such as the website, Outlook plug-in, or sync clients For wrapped Citrix Files apps: Users who log on to Citrix Files get redirected to Citrix Secure Hub for user authentication and to acquire a SAML token. After successful authentication, the Citrix Files mobile app sends the SAML token to ShareFile. After the initial logon, users can access the Citrix Files mobile app through SSO. They can also attach documents from ShareFile to Citrix Secure Mail mails without logging on each time. For non-wrapped Citrix Files clients: Users who log on to Citrix Files using a web browser or other Citrix Files client are redirected to Citrix Endpoint Management. Citrix Endpoint Management authenticates the users, who then acquire a SAML token which is sent to ShareFile. After the initial logon, users can access Citrix Files clients through SSO without logging on each time. To use Citrix Endpoint Management as a SAML identity provider (IdP) to ShareFile, you must configure Citrix Endpoint Management for use with Enterprise accounts, as described in this article. Or, you can configure Citrix Endpoint Management to work only with storage zone connectors. For more information, see ShareFile use with Citrix Endpoint Management. For a detailed reference architecture diagram, see . PrerequisitesComplete the following prerequisites before you can configure SSO with Citrix Endpoint Management and Citrix Files apps: Configure ShareFile accessBefore setting up SAML for ShareFile, provide ShareFile access information as follows:
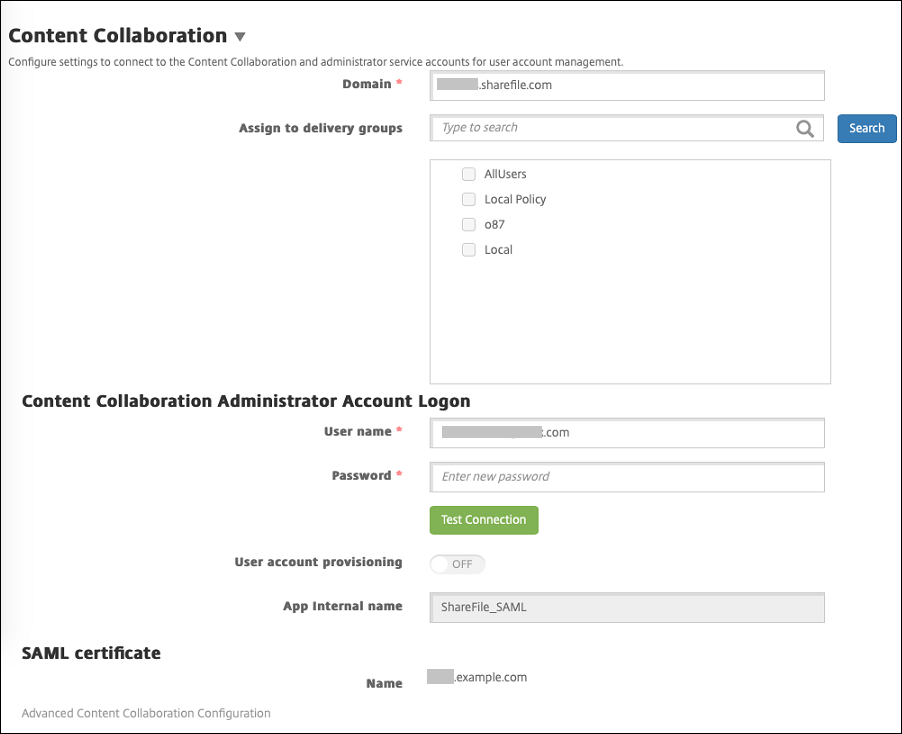
In the Citrix Endpoint Management web console, click Configure > ShareFile. The ShareFile configuration page appears.
Configure these settings:
Click Test Connection to verify that the user name and password for the ShareFile administrator account authenticate to the specified ShareFile account.
Click Save.
Citrix Endpoint Management syncs with ShareFile and updates the ShareFile settings ShareFile Issuer/Entity ID and Login URL.
The Configure > ShareFile page shows the App internal name. You need that name to complete the steps described later in [Modify the Citrix Files.com SSO settings] (#modify-the-citrix-filescom-sso-settings). Set up SAML for Wrapped Citrix Files MDX AppsYou don’t need to use NetScaler Gateway for single sign-on configuration with Citrix Files apps prepared with the MAM SDK. To configure access for non-wrapped Citrix Files clients, such as the website, Outlook plug-in, or the sync clients, see . To configure SAML for wrapped Citrix Files MDX apps:
Download the ShareFile for Citrix Endpoint Management clients. See ShareFile Tool/App Downloads.
Prepare the Citrix Files mobile app with the MAM SDK. For details, see the MAM SDK overview.
In the Citrix Endpoint Management console, upload the prepared Citrix Files mobile app. For information about uploading MDX apps, see To add an MDX app to Citrix Endpoint Management.
Verify the SAML settings: Log on to ShareFile with the administrator user name and password you configured earlier.
Verify that ShareFile and Citrix Endpoint Management are configured for the same time zone. Make sure that Citrix Endpoint Management shows the correct time for the configured time zone. If not, the SSO might fail. Validate the Citrix Files mobile app
On the user device, install and configure Citrix Secure Hub.
From the app store, download and install the Citrix Files mobile app.
Start the Citrix Files mobile app. Citrix Files starts without prompting for user name or password. Validate with Citrix Secure Mail
On the user device, if it has not already been done, install and configure Citrix Secure Hub.
From the app store, download, install, and set up Citrix Secure Mail.
Open a new email form and then tap Attach from ShareFile. Files available to attach to the email are shown without asking for a user name or password. Configure NetScaler Gateway for other Citrix Files clientsTo configure access for non-wrapped Citrix Files clients, such as the website, Outlook plug-in, or the sync clients: Configure NetScaler Gateway to support the use of Citrix Endpoint Management as a SAML identity provider as follows. Disable home page redirection. Create a Citrix Files session policy and profile. Configure policies on the NetScaler Gateway virtual server. Disable home page redirectionDisable the default behavior for requests that come through the /cginfra path. That action enables users to see the original requested internal URL instead of the configured home page.
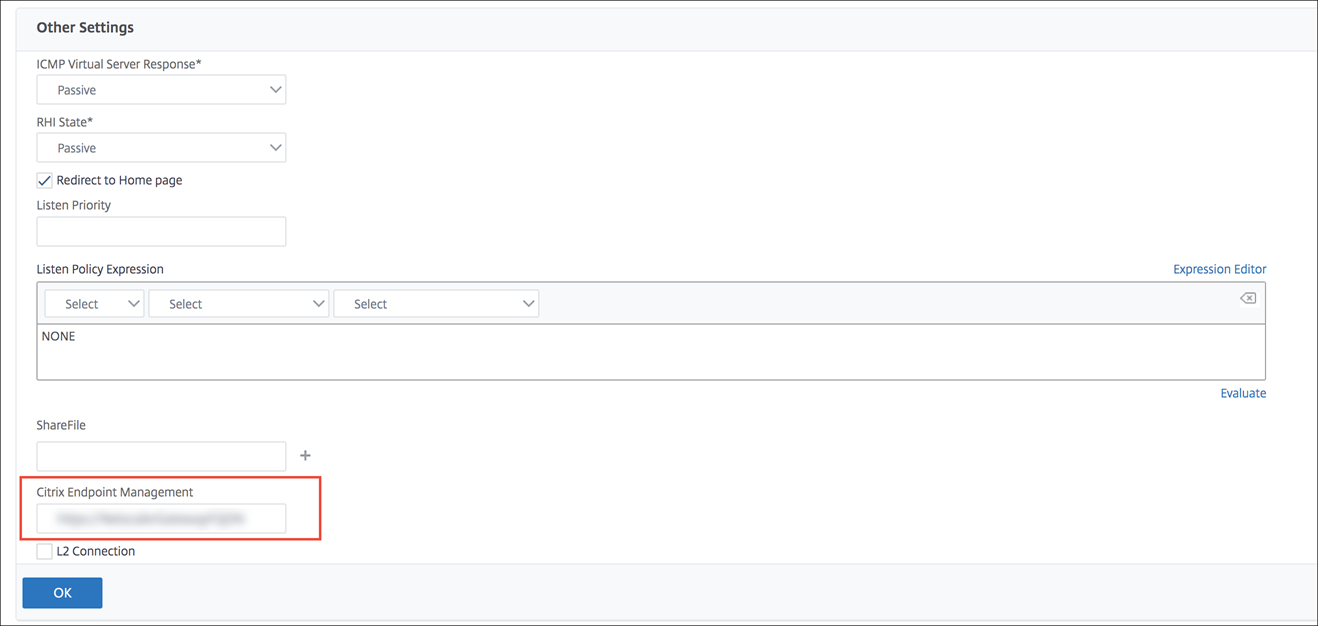
Edit the settings for the NetScaler Gateway virtual server that is used for Citrix Endpoint Management logons. In NetScaler Gateway, go to Other Settings and then clear the checkbox labeled Redirect to Home Page.
Under ShareFile (now called ShareFile), type your Citrix Endpoint Management internal server name and port number.
Under Citrix Endpoint Management, type your Citrix Endpoint Management URL. This configuration authorizes requests to the URL that you entered through the /cginfra path. Create a Citrix Files session policy and request profileConfigure these settings to create a Citrix Files session policy and request profile:
In the NetScaler Gateway configuration utility, in the left-hand navigation pane, click NetScaler Gateway > Policies > Session.
Create a session policy. On the Policies tab, click Add.
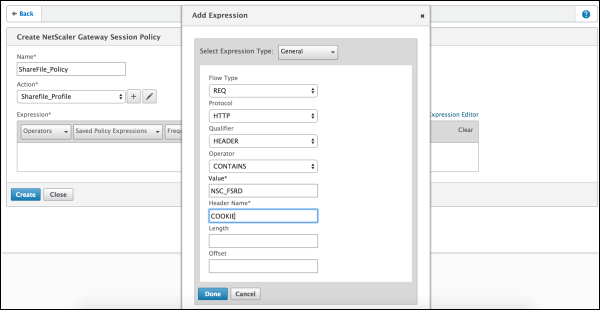
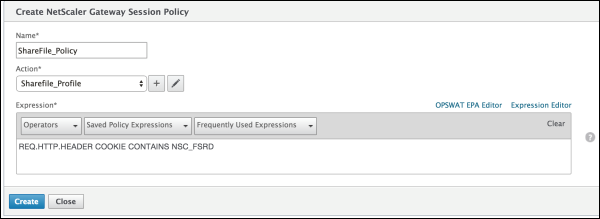
In the Name field, type ShareFile_Policy.
Create an action by clicking the + button. The Create NetScaler Gateway Session Profile page appears.
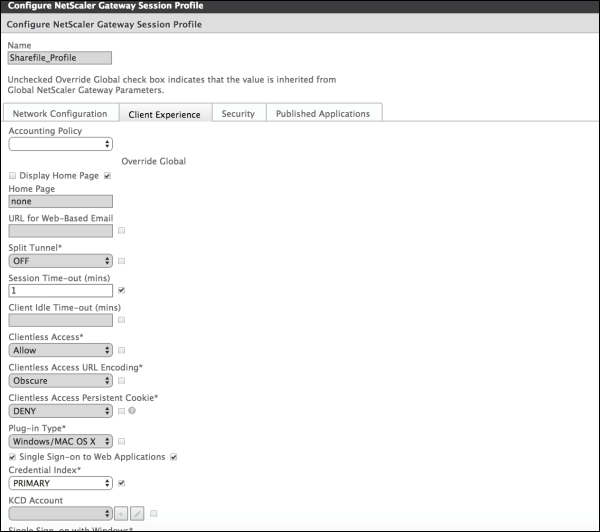
Configure these settings: Name: Type ShareFile_Profile. Click the Client Experience tab and then configure these settings: Home Page: Type none. Session Time-out (mins): Type 1. Single Sign-on to Web Applications: Select this setting. Credential Index: Click PRIMARY. Click the Published Applications tab.
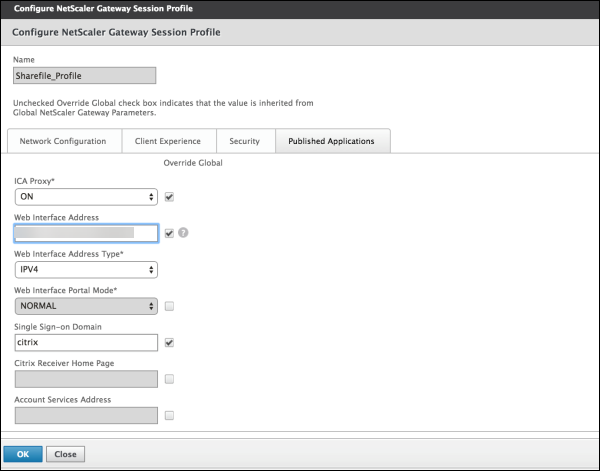
Configure these settings: ICA Proxy: Click On. Web Interface Address: Type your Citrix Endpoint Management server URL.
Single Sign-on Domain: Type your Active Directory domain name. When configuring the NetScaler Gateway Session Profile, the domain suffix for Single Sign-on Domain must match the Citrix Endpoint Management domain alias defined in LDAP.
Click Create to define the session profile.
Click Expression Editor.
Configure these settings: Value: Type NSC_FSRD. Header Name: Type COOKIE.
Click Create and then click Close.
Configure these settings on the NetScaler Gateway virtual server.
In the NetScaler Gateway configuration utility, in the left navigation pane, click NetScaler Gateway > Virtual Servers.
In the Details pane, click your NetScaler Gateway virtual server.
Click Edit.
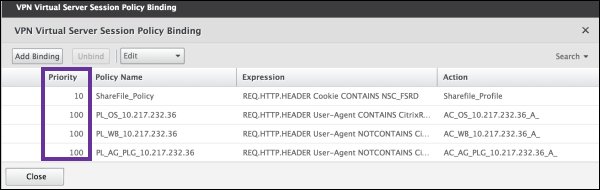
Click Configured policies > Session policies and then click Add binding.
Select ShareFile_Policy.
Edit the auto-generated Priority number for the selected policy so that it has the highest priority (the smallest number) in relation to any other policies listed. For example:
Click Done and then save the running NetScaler Gateway configuration. Modify the Citrix Files.com SSO settingsMake the following changes for both MDX and non-MDX Citrix Files apps. Important: A new number is appended to the internal application name: Each time you edit or recreate the Citrix Files app Each time you change the ShareFile settings in Citrix Endpoint Management As a result, you must also update the Login URL in the Citrix Files website to display the updated app name.
Log on to your ShareFile account (https://<subdomain>.sharefile.com) as a ShareFile administrator.
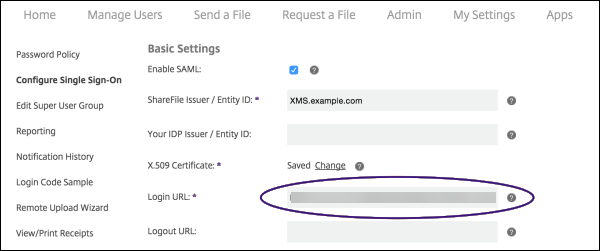
In the ShareFile web interface, click Admin and then select Configure Single Sign-on.
Edit the Login URL as follows: Here’s a sample Login URL before the edits: https://xms.citrix.lab/samlsp/websso.do?action=authenticateUser&app=ShareFile_SAML_SP&reqtype=1.
Insert the NetScaler Gateway virtual server external FQDN plus /cginfra/https/ in front of the Citrix Endpoint Management server FQDN and then add 8443 after the Citrix Endpoint Management FQDN. Here’s a sample of an edited URL: https://nsgateway.acme.com/cginfra/https/xms.citrix.lab:8443/samlsp/websso.do?action=authenticateUser&app=ShareFile_SAML_SP&reqtype=1
Change the parameter &app=ShareFile_SAML_SP to the internal Citrix Files application name. The internal name is ShareFile_SAML by default. However, every time you change your configuration, a number is appended to the internal name (ShareFile_SAML_2, ShareFile_SAML_3, and so on). You can look up the App internal name on the Configure > ShareFile page. Here’s a sample of an edited URL: https://nsgateway.acme.com/cginfra/https/xms.citrix.lab:8443/samlsp/websso.do?action=authenticateUser&app=ShareFile_SAML&reqtype=1
Add &nssso=true to the end of the URL. Here’s a sample of the final URL: https://nsgateway.acme.com/cginfra/https/xms.citrix.lab:8443/samlsp/websso.do?action=authenticateUser&app=ShareFile_SAML&reqtype=1&nssso=true.
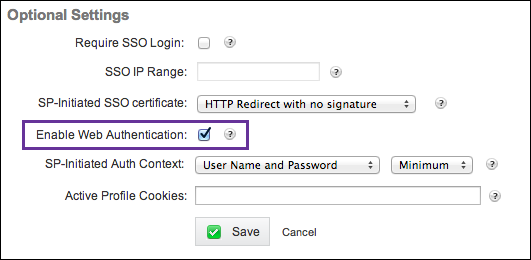
Under Optional Settings, select the Enable Web Authentication checkbox.
Do the following to validate the configuration.
Point your browser to https://<subdomain>sharefile.com/saml/login. You are redirected to the NetScaler Gateway logon form. If you are not redirected, verify the preceding configuration settings.
Enter the user name and password for the NetScaler Gateway and Citrix Endpoint Management environment that you configured. Your Citrix Files folders at <subdomain>.sharefile.com appear. If you do not see your Citrix Files folders, make sure that you entered the proper logon credentials.
The official version of this content is in English. Some of the Cloud Software Group documentation content is machine translated for your convenience only. Cloud Software Group has no control over machine-translated content, which may contain errors, inaccuracies or unsuitable language. No warranty of any kind, either expressed or implied, is made as to the accuracy, reliability, suitability, or correctness of any translations made from the English original into any other language, or that your Cloud Software Group product or service conforms to any machine translated content, and any warranty provided under the applicable end user license agreement or terms of service, or any other agreement with Cloud Software Group, that the product or service conforms with any documentation shall not apply to the extent that such documentation has been machine translated. Cloud Software Group will not be held responsible for any damage or issues that may arise from using machine-translated content.
DIESER DIENST KANN ÜBERSETZUNGEN ENTHALTEN, DIE VON GOOGLE BEREITGESTELLT WERDEN. GOOGLE LEHNT JEDE AUSDRÜCKLICHE ODER STILLSCHWEIGENDE GEWÄHRLEISTUNG IN BEZUG AUF DIE ÜBERSETZUNGEN AB, EINSCHLIESSLICH JEGLICHER GEWÄHRLEISTUNG DER GENAUIGKEIT, ZUVERLÄSSIGKEIT UND JEGLICHER STILLSCHWEIGENDEN GEWÄHRLEISTUNG DER MARKTGÄNGIGKEIT, DER EIGNUNG FÜR EINEN BESTIMMTEN ZWECK UND DER NICHTVERLETZUNG VON RECHTEN DRITTER. CE SERVICE PEUT CONTENIR DES TRADUCTIONS FOURNIES PAR GOOGLE. GOOGLE EXCLUT TOUTE GARANTIE RELATIVE AUX TRADUCTIONS, EXPRESSE OU IMPLICITE, Y COMPRIS TOUTE GARANTIE D'EXACTITUDE, DE FIABILITÉ ET TOUTE GARANTIE IMPLICITE DE QUALITÉ MARCHANDE, D'ADÉQUATION À UN USAGE PARTICULIER ET D'ABSENCE DE CONTREFAÇON. ESTE SERVICIO PUEDE CONTENER TRADUCCIONES CON TECNOLOGÍA DE GOOGLE. GOOGLE RENUNCIA A TODAS LAS GARANTÍAS RELACIONADAS CON LAS TRADUCCIONES, TANTO IMPLÍCITAS COMO EXPLÍCITAS, INCLUIDAS LAS GARANTÍAS DE EXACTITUD, FIABILIDAD Y OTRAS GARANTÍAS IMPLÍCITAS DE COMERCIABILIDAD, IDONEIDAD PARA UN FIN EN PARTICULAR Y AUSENCIA DE INFRACCIÓN DE DERECHOS. 本服务可能包含由 Google 提供技术支持的翻译。Google 对这些翻译内容不做任何明示或暗示的保证,DG游戏包括对准确性、可靠性的任何保证以及对适销性、特定用途的适用性和非侵权性的任何暗示保证。 このサービスには、Google が提供する翻訳が含まれている可能性があります。Google は翻訳について、明示的か黙示的かを問わず、精度と信頼性に関するあらゆる保証、および商品性、特定目的への適合性、第三者の権利を侵害しないことに関するあらゆる黙示的保証を含め、一切保証しません。 ESTE SERVIÇO PODE CONTER TRADUÇÕES FORNECIDAS PELO GOOGLE. O GOOGLE SE EXIME DE TODAS AS GARANTIAS RELACIONADAS COM AS TRADUÇÕES, EXPRESSAS OU IMPLÍCITAS, INCLUINDO QUALQUER GARANTIA DE PRECISÃO, CONFIABILIDADE E QUALQUER GARANTIA IMPLÍCITA DE COMERCIALIZAÇÃO, ADEQUAÇÃO A UM PROPÓSITO ESPECÍFICO E NÃO INFRAÇÃO. (责任编辑:) |